Die vorliegende Übersetzung wurde maschinell erstellt. Im Falle eines Konflikts oder eines Widerspruchs zwischen dieser übersetzten Fassung und der englischen Fassung (einschließlich infolge von Verzögerungen bei der Übersetzung) ist die englische Fassung maßgeblich.
Implementieren Sie die auf Microsoft Entra ID basierende Authentifizierung in einer modernisierten Mainframe-Anwendung von AWS Blu Age
Vishal Jaswani und Rimpy Tewani, Amazon Web Services
Übersicht
Mainframe-Anwendungen, die mithilfe von Refactoring-Mustern modernisiert werden, wie die von AWS Mainframe Modernization Refactor mit AWS Blu Age, erfordern eine sorgfältige Integration der Authentifizierungsmechanismen in die neue Anwendungsarchitektur. Diese Integration wird in der Regel erst im Anschluss an die Modernisierung angegangen. Die Aufgabe kann komplex sein und beinhaltet häufig die Migration oder Externalisierung vorhandener Authentifizierungssysteme, um sie an moderne Sicherheitsstandards und Cloud-native Praktiken anzupassen. Entwickler müssen überlegen, wie sie die Authentifizierung effektiv implementieren können, während sie gleichzeitig die Einschränkungen der Laufzeitumgebung und der Bibliotheken der modernisierten Anwendung einhalten. AWS Bietet nach der Modernisierung Möglichkeiten, wie Sie Ihren modernen AWS Blu-Age-Code einfacher in Identitäts- und Zugriffsverwaltungssysteme wie Amazon Cognito und Microsoft Entra ID
Dieses Muster erklärt, wie Sie einen Authentifizierungsmechanismus in Ihrer modernisierten Anwendung implementieren können, wenn der Authentifizierungsanbieter Microsoft Entra ID ist, ohne Zeit für Recherchen und Tests aufzuwenden. Das Muster bietet:
Praxiserprobte und relevante Angular-Bibliotheken aus der Microsoft Authentication Library (MSAL) und anderen Microsoft Entra ID-Dokumentationen, die für die Authentifizierungsimplementierung unerlässlich sind.
Konfigurationen, die auf der AWS Blu Age Runtime erforderlich sind, um Spring Security mithilfe von 2.0 zu aktivieren. OAuth
Eine Bibliothek, die die Identitäten authentifizierter Benutzer erfasst und an die AWS Blu Age Runtime weitergibt.
Sicherheitsmaßnahmen, deren Implementierung wir empfehlen.
Tipps zur Fehlerbehebung für häufig auftretende Probleme mit dem Microsoft Entra ID-Setup.
Anmerkung
Dieses Muster verwendet die AWS Blu OAuth Age-Erweiterungsbibliothek, die Kunden im Rahmen ihrer AWS Professional Services-Vereinbarung
Voraussetzungen und Einschränkungen
Voraussetzungen
Eine modernisierte Anwendung, die mit den Refactoring-Tools für die Mainframe-Modernisierung von AWS Blu Age entwickelt wurde. Dieses Muster dient CardDemo
als Beispiel für eine Open-Source-Mainframe-Anwendung. Die AWS Blu OAuth Age-Erweiterungsbibliothek, die Ihnen das AWS Blu Age-Team im Rahmen Ihres Engagements bei AWS Professional Services
zur Verfügung stellt. Aktiv AWS-Konto für die Bereitstellung und das Testen der modernisierten Anwendung.
Vertrautheit mit AWS Blu Age-Konfigurationsdateien und den Grundlagen von Microsoft Entra ID.
Einschränkungen
Dieses Muster deckt die OAuth 2.0-Authentifizierung und grundlegende tokenbasierte Autorisierungsabläufe ab. Fortgeschrittene Autorisierungsszenarien und differenzierte Zugriffskontrollmechanismen sind nicht im Geltungsbereich enthalten.
Einige AWS-Services sind nicht in allen verfügbar. AWS-Regionen Informationen zur Verfügbarkeit in den einzelnen Regionen finden Sie AWS-Services unter Nach Regionen
. Informationen zu bestimmten Endpunkten finden Sie unter Dienstendpunkte und Kontingente. Wählen Sie dort den Link für den Dienst aus.
Produktversionen
Dieses Muster wurde entwickelt unter Verwendung von:
AWS Blu Age Runtime Version 4.1.0 (das Muster funktioniert auch mit späteren Versionen, die abwärtskompatibel sind)
MSAL-Bibliothek, Version 3.0.23
Version 17 des Java-Entwicklungskits (JDK)
Eckige Version 16.1
Architektur
Quelltechnologie-Stack
In typischen Mainframe-Umgebungen wird die Authentifizierung über Benutzerprofile implementiert. Diese Profile identifizieren Benutzer im System, definieren, wer sich anmelden kann, und geben an, welche Funktionen Benutzer mit Systemressourcen ausführen können. Benutzerprofile werden von Sicherheitsbeauftragten oder Sicherheitsadministratoren verwaltet.
Zieltechnologie-Stack
Microsoft Entra ID
Modernisiertes Backend auf Basis von Java Spring Boot
AWS Blue Age Runtime
Spring Security mit OAuth 2.0
Angular Single-Page-Anwendung (SPA)
Zielarchitektur
AWS Blu Age Runtime unterstützt standardmäßig die OAuth 2.0-basierte Authentifizierung, sodass das Pattern diesen Standard zum Schutz des Backends APIs verwendet.
Das folgende Diagramm veranschaulicht den Prozessablauf.
Anmerkung
Das Diagramm enthält Amazon Aurora als Beispiel für die Datenbankmodernisierung, obwohl Aurora nicht in den Schritten für dieses Muster enthalten ist.
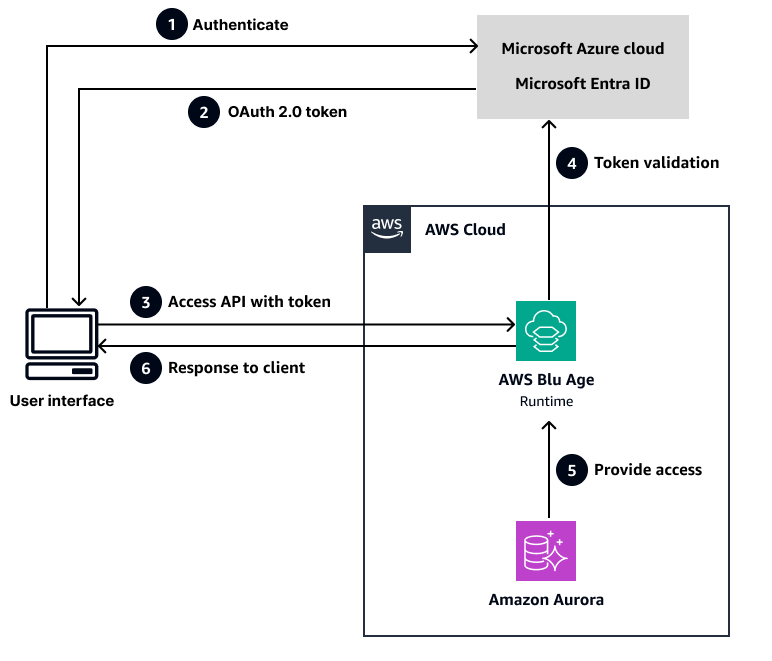
Wobei:
Ein Benutzer versucht, sich mit Microsoft Entra ID zu authentifizieren.
Microsoft Entra ID gibt Aktualisierungs-, Zugriffs- und ID-Tokens zurück, die die Anwendung bei nachfolgenden Aufrufen verwendet.
Der MSAL-Interceptor fügt das Zugriffstoken in den
AuthorizationHeader einer HTTPS-Anfrage ein, um die Blu Age Runtime AWS aufzurufen.Die AWS Blu
extension-oauthAge-Bibliothek extrahiert die Benutzerinformationen mithilfe einer AWS Blu Age Runtime-Konfigurationsdatei (application-main.yml) aus dem Header und platziert diese Informationen in einemSharedContextObjekt, sodass die Geschäftslogik sie verarbeiten kann.Anmerkung
SharedContextist eine von AWS Blu Age bereitgestellte Laufzeitkomponente, die den Anwendungskontext und die Statusinformationen in der gesamten modernisierten Anwendung verwaltet. Weitere Informationen zu den Komponenten und Updates von AWS Blu Age Runtime finden Sie in den Versionshinweisen zu AWS Blu Age in der AWS Mainframe Modernization Dokumentation. Weitere Informationen zurapplication-main.ymlDatei finden Sie in der AWS Mainframe Modernization Dokumentation unter Konfiguration für AWS Blu Age Runtime einrichten.Die AWS Blu Age Runtime prüft, ob das Token vorhanden ist.
Wenn das Token vorhanden ist, überprüft es die Gültigkeit des Tokens, indem es mit der Microsoft Entra ID kommuniziert.
Wenn das Token nicht vorhanden ist, gibt die AWS Blu Age Runtime einen Fehler mit dem HTTP-Statuscode 403 zurück.
Wenn das Token gültig ist, ermöglicht die AWS Blue Age Runtime die Fortsetzung der Geschäftslogik. Wenn das Token ungültig ist, gibt die AWS Blu Age Runtime einen Fehler mit dem HTTP-Statuscode 403 zurück.
OAuth 2.0-Arbeitsablauf
Ein allgemeines Diagramm des OAuth 2.0-Workflows finden Sie in der Microsoft Entra-Dokumentation
Tools
AWS-Services
AWS Mainframe Modernizationstellt Tools und Ressourcen bereit, die Sie bei der Planung und Implementierung der Migration und Modernisierung von Mainframes zu AWS verwalteten Laufzeitumgebungen unterstützen. Sie können die von AWS Blu Age bereitgestellten Refactoring-Funktionen dieses Services nutzen, um Ihre älteren Mainframe-Anwendungen zu konvertieren und zu modernisieren.
Code-Repository
Die CardDemo Anwendung wurde aktualisiert, um die Integration mit Microsoft Entra ID zu demonstrieren. Sie können auf den Code für dieses Muster aus dem GitHub Repository
Backend-Konfiguration
Dieses Muster erfordert Änderungen an der application-main.yml Konfigurationsdatei, um Spring Security mithilfe von OAuth 2.0 in der Backend-Anwendung zu aktivieren. Die .yml Datei sieht wie folgt aus:
gapwalk-application.security: enabled gapwalk-application: security: identity: oauth issuerUri: ${issuerUrl} claim: claims: - claimName: upn claimMapValue: username spring: autoconfigure: exclude: - org.springframework.boot.autoconfigure.security.oauth2.client.servlet.OAuth2ClientAutoConfiguration - org.springframework.boot.autoconfigure.security.oauth2.resource.servlet.OAuth2ResourceServerAutoConfiguration security: oauth2: client: registration: azure: client-id: {clientId} client-secret: ${clientSecret} provider: azure authorization-grant-type: authorization_code redirect-uri: ${redirectUri} scope: openid provider: azure: authorization-uri: ${gapwalk-application.security.issuerUri}/oauth2/v2.0/authorize token-uri: ${gapwalk-application.security.issuerUri}/oauth2/v2.0/token jwk-set-uri: ${gapwalk-application.security.issuerUri}/discovery/v2.0/keys resourceserver: jwt: jwk-set-uri: ${gapwalk-application.security.issuerUri}/discovery/v2.0/keys
AWS Blu OAuth Age-Erweiterungsfilterbibliothek
Die AWS Blu OAuth Age-Erweiterungsbibliothek wird vom AWS Blu Age-Team während Ihres Aufenthalts bei AWS Professional Services
Diese Bibliothek liest die claim.claims Konfiguration in der application-main.yml Datei, die im vorherigen Codeblock gezeigt wurde. Diese Konfiguration ist eine Liste. Jedes Element in der Liste bietet zwei Werte: claimName undclaimMapValue. claimNamesteht für einen Schlüsselnamen in einem vom Frontend gesendeten JSON Web Token (JWT) und claimMapValue ist der Name des Schlüssels in. SharedContext Wenn Sie beispielsweise die Benutzer-ID im Backend erfassen möchten, legen claimName Sie den Schlüsselnamen im JWT fest, der die von Microsoft bereitgestellte Entra-ID enthält, und legen Sie den Schlüsselnamen fest, claimMapValue um die Benutzer-ID im Backend-Code abzurufen. userId
Wenn Sie beispielsweise angeben, können Sie UserId den folgenden Code verwendenclaimMapValue, um die Benutzer-ID zu extrahieren:
SharedContext.get().getValue("userId", [UserId]);
Bewährte Methoden
Berücksichtigen Sie bei der Implementierung dieses Musters die folgenden wichtigen Sicherheitsüberlegungen.
Wichtig
Dieses Muster bietet eine Grundlage für die Integration der Authentifizierung. Wir empfehlen Ihnen, zusätzlich zu den in diesem Abschnitt beschriebenen Sicherheitsmaßnahmen auf der Grundlage Ihrer Geschäftsanforderungen zu ergreifen, bevor Sie das Produkt in der Produktion einsetzen.
AWS Sicherheit der Konfiguration.Verschieben Sie sensible Konfigurationswerte von
application-main.ymlnach AWS Secrets Manager. Konfigurieren Sie beispielsweise die folgenden Eigenschaften mithilfe von Secrets Manager:security: oauth2: client: registration: azure: client-id: {clientId} client-secret: ${clientSecret}Weitere Informationen darüber, wie Sie Secrets Manager zur Konfiguration von AWS Blu Age-Parametern verwenden können, finden Sie in der AWS Mainframe Modernization Dokumentation unter AWS Blu Age Runtime Secrets.
Schutz der Runtime-Umgebung. Konfigurieren Sie die modernisierte Anwendungsumgebung mit geeigneten AWS Sicherheitskontrollen:
server: tomcat: remoteip: protocol-header: X-Forwarded-Proto remote-ip-header: X-Forwarded-For forward-headers-strategy: NATIVECloudWatch Amazon-Protokollierung. Erwägen Sie, die Datei hinzuzufügen
logback-spring.xml to src/main/resources:<configuration> <appender name="CLOUDWATCH" class="com.amazonaws.services.logs.logback.CloudWatchAppender"> <logGroup>/aws/bluage/application</logGroup> <logStream>${AWS_REGION}-${ENVIRONMENT}</logStream> <layout> <pattern>%d{yyyy-MM-dd HH:mm:ss} [%thread] %-5level %logger{36} - %msg%n</pattern> </layout> </appender> <root level="INFO"> <appender-ref ref="CLOUDWATCH"/> </root> </configuration>Informationen zur Aktivierung der Ablaufverfolgung mit CloudWatch finden Sie in der CloudWatch Dokumentation unter Aktivieren der Ablaufverfolgung zur Protokollierung der Korrelation.
Konfiguration und Handhabung von Tokens. Konfigurieren Sie die Token-Gültigkeitsdauer in Microsoft Entra ID entsprechend Ihren Sicherheitsanforderungen. Legen Sie fest, dass Zugriffstoken innerhalb von 1 Stunde ablaufen, und aktualisieren Sie Tokens so, dass sie innerhalb von 24 Stunden ablaufen. Stellen Sie in der AWS Blu Age Runtime-Konfiguration (
application-main.yml) sicher, dass die JWT-Validierung ordnungsgemäß mit den exakten Aussteller-URI- und Zielgruppenwerten aus Ihrer Entra ID-Anwendungsregistrierung konfiguriert ist.Wenn ein Token abläuft und aktualisiert wird:
Der Error Interceptor der Angular-Anwendung verarbeitet die 401-Antwort, indem er über MSAL ein neues Token erhält.
Das neue Token wird mit der nachfolgenden Anfrage gesendet.
Der OAuth Filter der AWS Blu Age Runtime validiert das neue Token und aktualisiert es automatisch
SharedContextmit den aktuellen Benutzerinformationen. Dadurch wird sichergestellt, dass die Geschäftslogik überSharedContext.get().getValue()Aufrufe weiterhin Zugriff auf den gültigen Benutzerkontext hat.
Weitere Informationen zu den AWS Blu Age Runtime-Komponenten und ihren Updates finden Sie in den AWS Blu Age-Versionshinweisen.
AWS Blu Age Runtime-Sicherheit. Die von AWS Blu Age bereitgestellte
oauth2-extBibliothek muss sich am richtigen Speicherort für das gemeinsam genutzte Verzeichnis ({app-server-home}/shared/) mit den richtigen Dateiberechtigungen befinden. Stellen Sie sicher, dass die Bibliothek erfolgreich Benutzerinformationen extrahiert, JWTs indem Sie dieSharedContextObjektpopulation in Ihren Protokollen überprüfen.Spezifische Anspruchskonfiguration. Definieren Sie in
application-main.ymlexplizit die Ansprüche, die Sie von Microsoft Entra ID benötigen. Um beispielsweise die E-Mail-Adresse und die Rollen des Benutzers zu erfassen, geben Sie Folgendes an:gapwalk-application: security: claim: claims: - claimName: upn claimMapValue: username - claimName: roles claimMapValue: userRoles - claimName: email claimMapValue: userEmailBehandlung von Fehlern. Fügen Sie eine Fehlerbehandlung hinzu, um Authentifizierungsfehler in Ihrer Angular-Anwendung zu beheben; zum Beispiel:
@Injectable() export class AuthErrorInterceptor implements HttpInterceptor { intercept(request: HttpRequest<any>, next: HttpHandler): Observable<HttpEvent<any>> { return next.handle(request).pipe( catchError((error: HttpErrorResponse) => { if (error.status === 401) { // Handle token expiration this.authService.login(); } if (error.status === 403) { // Handle unauthorized access this.router.navigate(['/unauthorized']); } return throwError(() => error); }) ); } }Konfiguration des Sitzungs-Timeouts. Konfigurieren Sie die Einstellungen für das Sitzungstimeout sowohl in der AWS Blu Age Runtime als auch in der Microsoft Entra ID. Fügen Sie Ihrer Datei beispielsweise den folgenden Code hinzu
application-main.yml:server: servlet: session: timeout: 3600 # 1 hour in secondsMsalGuard. Sie müssen die MsalGuard Funktion für alle geschützten Routen implementieren, um unbefugten Zugriff zu verhindern. Zum Beispiel:
const routes: Routes = [ { path: '', redirectTo: '/transaction-runner', pathMatch: 'full' }, { path: 'transaction-runner', component: TransactionRunnerComponent, canActivate:guards }, { path: 'user-info', component: UserInfoComponent, canActivate:guards }, { path: 'term/:transid/:commarea', component: TermComponent, canActivate:guards }, { path: 'code', component: TransactionRunnerComponent } ];Routen, die nicht MsalGuard geschützt sind, sind ohne Authentifizierung zugänglich, wodurch möglicherweise vertrauliche Funktionen offengelegt werden. Stellen Sie sicher, dass alle Routen, für die eine Authentifizierung erforderlich ist, die Guards in ihrer Konfiguration enthalten.
Epen
| Aufgabe | Beschreibung | Erforderliche Fähigkeiten |
|---|---|---|
Richten Sie ein Microsoft Azure-Konto ein, um eine Entra-ID zu erstellen. | Optionen und Anweisungen finden Sie auf der Microsoft Azure-Website | App-Developer |
Richten Sie in Ihrer Anwendung eine Microsoft Entra ID ein. |
| App-Developer |
| Aufgabe | Beschreibung | Erforderliche Fähigkeiten |
|---|---|---|
Klonen Sie das GitHub Repository, um den für die Authentifizierung erforderlichen Angular-Code zu erhalten. | Führen Sie den folgenden Befehl aus, um das GitHub Repository
| App-Developer |
Stellen Sie den modernisierten AWS Blu-Age-Code auf einem Tomcat-Server bereit, um die Authentifizierung zu implementieren. | Um die lokale Umgebung einzurichten, die Tomcat und den Angular-Entwicklungsserver umfasst, folgen Sie den Installationsschritten, die das AWS Blu Age-Team im Rahmen Ihrer Kundenbindung mit AWS Professional Services bereitgestellt hat. | App-Developer |
| Aufgabe | Beschreibung | Erforderliche Fähigkeiten |
|---|---|---|
Aktivieren Sie die AWS Blu Age Runtime-Sicherheit, um die AWS Blu Age REST-API-Endpunkte zu schützen. | Konfigurieren Sie die
| App-Developer |
Integrieren Sie den Beispielcode aus Ihrer lokalen Umgebung in Ihre modernisierte Angular-Codebasis von Blu Age. | Informationen darüber, wie Sie das Beispiel in Ihre modernisierte AWS Blu Age-Angular-Codebasis integrieren können, finden Sie im Abschnitt Code-Repository weiter oben in diesem Muster. | App-Developer |
Platzieren Sie die | Platzieren Sie die
| App-Developer |
| Aufgabe | Beschreibung | Erforderliche Fähigkeiten |
|---|---|---|
Stellen Sie die Frontend-Anwendung bereit. | Führen Sie die folgenden Befehle aus, um die Frontend-Anwendung lokal zu starten:
AnmerkungDurch das Hinzufügen des | App-Developer |
Starten Sie die Backend-Anwendung. | Starten Sie den Tomcat-Server in Eclipse. | App-Developer |
| Aufgabe | Beschreibung | Erforderliche Fähigkeiten |
|---|---|---|
Testen Sie die Anmeldefunktion. | Rufen Sie die lokal bereitgestellte Anwendung unter auf, AnmerkungHTTP wird hier zu Demonstrationszwecken verwendet. In einer Produktionsumgebung oder einer anderen öffentlich zugänglichen Umgebung müssen Sie aus Sicherheitsgründen HTTPS verwenden. Selbst für die lokale Entwicklung empfehlen wir, dass Sie, wenn möglich, HTTPS einrichten. Die Microsoft-Anmeldeaufforderung sollte angezeigt werden, und Benutzer, die in Microsoft Entra ID konfiguriert sind, sollten auf die Anwendung zugreifen können. | App-Developer |
Testen Sie den Autorisierungsheader in der Anfrage. | AnmerkungIn den folgenden Schritten wird die CardDemo
| App-Developer |
Testen Sie die Abmeldefunktion. | Wählen Sie Quit, um sich abzumelden, und versuchen Sie erneut, auf die Anwendung zuzugreifen. Es sollte eine neue Anmeldeaufforderung angezeigt werden. | App-Developer |
Fehlerbehebung
| Problem | Lösung |
|---|---|
Das von Microsoft Entra ID ausgegebene Token ist nicht mit der Spring Boot OAuth 2.0-Sicherheit kompatibel. | Eine Lösung für das Problem finden Sie im OAuth Blog unter Microsoft OAuth Entra ID Flow |
Allgemeine Fragen zu Tokens. |
Zugehörige Ressourcen
Informationen zur Funktionsweise von OAuth 2.0 finden Sie auf der OAuth 2.0-Website
. Einen Überblick über die Microsoft Authentication Library (MSAL) finden Sie in der Microsoft Entra-Dokumentation
. Informationen zu Benutzerprofilen auf einem AS/400-System finden Sie im IBM i (AS400) -Tutorial
. Informationen zum Authentifizierungsablauf OAuth 2.0 und OpenID Connect (OIDC) in der Microsoft Identity Platform finden Sie in der Microsoft Entra-Dokumentation
.