Terjemahan disediakan oleh mesin penerjemah. Jika konten terjemahan yang diberikan bertentangan dengan versi bahasa Inggris aslinya, utamakan versi bahasa Inggris.
Mengatur set izin untuk beberapa akun dengan menggunakan Account Factory untuk Terraform
Anand Krishna Varanasi dan Siamak Heshmati, Amazon Web Services
Ringkasan
Pola ini membantu Anda mengintegrasikan AWS Control Tower Account Factory Terraform (AFT) dengan untuk mengonfigurasi izin untuk beberapa AWS IAM Identity Center Akun AWS pada skala besar. Pendekatan ini menggunakan AWS Lambda fungsi kustom untuk mengotomatiskan penetapan set izin ke Akun AWS yang dikelola sebagai organisasi. Ini merampingkan proses karena tidak memerlukan intervensi manual dari tim teknik platform Anda. Solusi ini dapat meningkatkan efisiensi operasional, keamanan dan konsistensi. Ini mempromosikan proses orientasi yang aman dan terstandarisasi AWS Control Tower, sehingga sangat diperlukan bagi perusahaan yang memprioritaskan kelincahan dan keandalan untuk infrastruktur cloud mereka.
Prasyarat dan batasan
Prasyarat
Akun AWS, dikelola melalui AWS Control Tower. Untuk informasi selengkapnya, lihat Memulai dengan AWS Control Tower.
Account Factory untuk Terraform, digunakan di akun khusus di lingkungan Anda. Untuk informasi selengkapnya, lihat Menerapkan AWS Control Tower Account Factory untuk Terraform.
Instance IAM Identity Center, disiapkan di lingkungan Anda. Untuk informasi selengkapnya, lihat Memulai Pusat Identitas IAM.
Grup Pusat Identitas IAM aktif, dikonfigurasi. Untuk informasi selengkapnya, lihat Menambahkan grup ke grup Direktori Pusat Identitas IAM.
Python versi 3.9 atau yang lebih baru, diinstal
Batasan
Solusi ini hanya dapat digunakan dengan akun yang dikelola melalui AWS Control Tower. Solusi ini digunakan dengan menggunakan Account Factory untuk Terraform.
Pola ini tidak termasuk instruksi untuk mengatur federasi identitas dengan sumber identitas. Untuk informasi selengkapnya tentang cara menyelesaikan pengaturan ini, lihat tutorial sumber identitas Pusat Identitas IAM di dokumentasi Pusat Identitas IAM.
Arsitektur
Ikhtisar AFT
AFT menyiapkan pipeline Terraform yang membantu Anda menyediakan dan menyesuaikan akun Anda. AWS Control Tower AFT mengikuti GitOps model yang mengotomatiskan proses penyediaan akun di. AWS Control Tower Anda membuat file Terraform permintaan akun dan memasukkannya ke repositori. Ini memulai alur kerja AFT untuk penyediaan akun. Setelah penyediaan akun selesai, AFT dapat secara otomatis menjalankan langkah-langkah penyesuaian tambahan. Untuk informasi selengkapnya, lihat arsitektur AFT dalam AWS Control Tower dokumentasi.
AFT menyediakan repositori utama berikut:
aft-account-request— Repositori ini berisi kode Terraform untuk membuat atau memperbarui. Akun AWSaft-account-customizations— Repositori ini berisi kode Terraform untuk membuat atau menyesuaikan sumber daya berdasarkan per akun.aft-global-customizations— Repositori ini berisi kode Terraform untuk membuat atau menyesuaikan sumber daya untuk semua akun, dalam skala besar.aft-account-provisioning-customizations— Repositori ini mengelola kustomisasi yang diterapkan hanya untuk akun tertentu yang dibuat oleh dan dikelola dengan AFT. Misalnya, Anda dapat menggunakan repositori ini untuk menyesuaikan penetapan pengguna atau grup di Pusat Identitas IAM atau untuk mengotomatiskan penutupan akun.
Ikhtisar solusi
Solusi khusus ini mencakup mesin AWS Step Functions status dan AWS Lambda fungsi yang menetapkan set izin untuk pengguna dan grup untuk beberapa akun. Mesin status yang digunakan melalui pola ini beroperasi bersama dengan mesin status AFT aft_account_provisioning_customizations yang sudah ada sebelumnya. Pengguna mengirimkan permintaan untuk memperbarui tugas pengguna dan grup IAM Identity Center baik saat baru Akun AWS dibuat atau setelah akun dibuat. Mereka melakukan ini dengan mendorong perubahan ke aft-account-request repositori. Permintaan untuk membuat atau memperbarui akun memulai aliran di Amazon DynamoDB Streams. Ini memulai fungsi Lambda, yang memperbarui pengguna dan grup Pusat Identitas IAM untuk target. Akun AWS
Berikut ini adalah contoh parameter yang dapat Anda berikan dalam fungsi Lambda untuk penetapan set izin untuk menargetkan pengguna dan grup:
custom_fields = { "InstanceArn" = "<Organization ID>", "PermissionSetArn" = "<Permission set ARN>", "PrincipalId" = "<Principal ID>", }
Berikut ini adalah parameter dalam pernyataan ini:
InstanceArn— Nama Sumber Daya Amazon (ARN) organisasiPermissionSetArn— ARN dari set izinPrincipalId— Pengidentifikasi pengguna atau grup di Pusat Identitas IAM tempat set izin akan diterapkan
catatan
Anda harus membuat set izin target, pengguna, dan grup sebelum menjalankan solusi ini.
Meskipun InstanceArn nilainya harus tetap konsisten, Anda dapat memodifikasi fungsi Lambda untuk menetapkan beberapa set izin ke beberapa identitas target. Parameter untuk set izin harus diakhiriPermissionSetArn, dan parameter untuk pengguna dan grup harus diakhiriPrincipalId. Anda harus mendefinisikan kedua atribut. Berikut ini adalah contoh cara mendefinisikan beberapa set izin dan target pengguna dan grup:
custom_fields = { "InstanceArn" = "<Organization ID>", "AdminAccessPermissionSetArn" = "<Admin privileges permission set ARN>", "AdminAccessPrincipalId" = "<Admin principal ID>", "ReadOnlyAccessPermissionSetArn" = "<Read-only privileges permission set ARN>", "ReadOnlyAccessPrincipalId" = "<Read-only principal ID>", }
Diagram berikut menunjukkan step-by-step alur kerja tentang cara solusi memperbarui set izin untuk pengguna dan grup dalam target Akun AWS pada skala besar. Saat pengguna memulai permintaan pembuatan akun, AFT memulai mesin status aft-account-provisioning-framework Step Functions. Mesin status ini memulai fungsi extract-alternate-sso Lambda. Fungsi Lambda menetapkan set izin untuk pengguna dan grup dalam target. Akun AWS Pengguna atau grup ini dapat berasal dari sumber identitas yang dikonfigurasi di IAM Identity Center. Contoh sumber identitas termasuk Okta, Active Directory, atau Ping Identity.
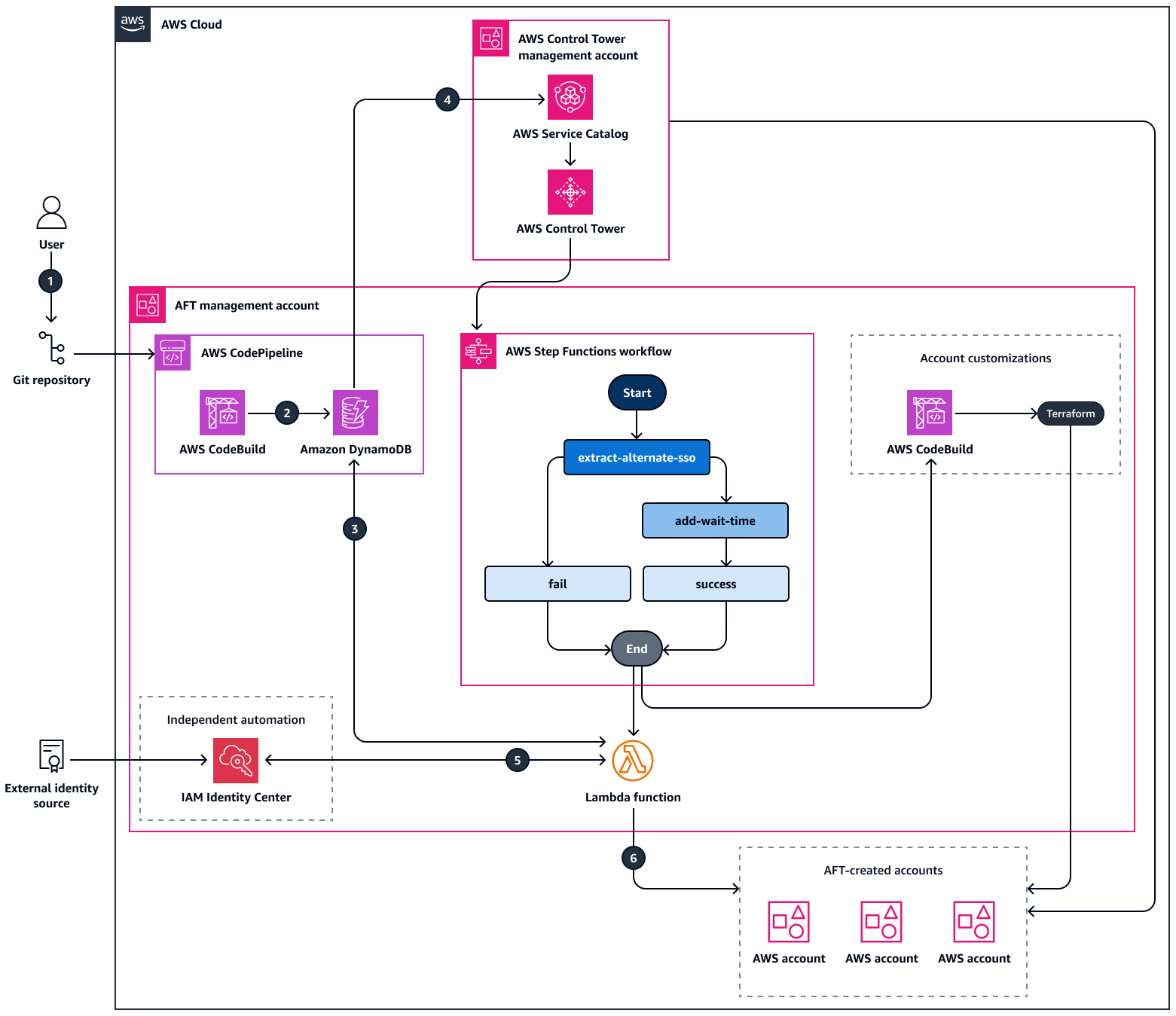
Diagram menunjukkan alur kerja berikut saat akun baru dibuat:
Seorang pengguna mendorong
custom_fieldsperubahan keaft-account-requestrepositori.AWS CodePipeline memulai AWS CodeBuild pekerjaan yang merekam metadata yang ditentukan pengguna ke dalam tabel Amazon
aft-request-auditDynamoDB. Tabel ini memiliki atribut untuk merekam metadata yang ditentukan pengguna.ddb_event_nameAtribut mendefinisikan jenis operasi AFT:Jika nilainya
INSERT, maka solusi akan menetapkan izin yang disetel ke identitas target saat yang baru Akun AWS dibuat.Jika nilainya
UPDATE, maka solusi akan menetapkan izin yang disetel ke identitas target setelah dibuat. Akun AWS
Amazon DynamoDB Streams memulai
aft_alternate_sso_extractfungsi Lambda.Fungsi
aft_alternate_sso_extractLambda mengasumsikan peran AWS Identity and Access Management (IAM) dalam akun manajemen. AWS Control TowerFungsi Lambda menetapkan set izin ke pengguna dan grup target dengan membuat panggilan API AWS SDK untuk Python (Boto3) create_account_assignment
ke IAM Identity Center. Ini mengambil set izin dan penetapan identitas dari tabel Amazon aft-request-auditDynamoDB.Ketika alur kerja Step Functions selesai, set izin ditetapkan ke identitas target.
Otomatisasi dan skala
AFT beroperasi pada skala dengan menggunakan Layanan AWS seperti CodePipeline,, DynamoDB AWS CodeBuild, dan Lambda, yang sangat skalabel. Untuk otomatisasi tambahan, Anda dapat mengintegrasikan solusi ini dengan tiket atau sistem manajemen masalah, seperti Jira. Untuk informasi selengkapnya, lihat bagian Informasi tambahan dari pola ini.
Alat
Layanan AWS
Account Factory for Terraform (AFT) adalah alat utama dalam solusi ini.
aft-account-provisioning-customizationsRepositori berisi kode Terraform untuk membuat penyesuaian, seperti penugasan pengguna atau grup Pusat Akun AWS Identitas IAM khusus.Amazon DynamoDB adalah layanan database NoSQL yang dikelola sepenuhnya yang menyediakan kinerja yang cepat, dapat diprediksi, dan terukur.
AWS Lambdaadalah layanan komputasi yang membantu Anda menjalankan kode tanpa perlu menyediakan atau mengelola server. Ini menjalankan kode Anda hanya bila diperlukan dan skala secara otomatis, jadi Anda hanya membayar untuk waktu komputasi yang Anda gunakan.
AWS Step Functionsadalah layanan orkestrasi tanpa server yang membantu Anda menggabungkan AWS Lambda fungsi dan lainnya Layanan AWS untuk membangun aplikasi bisnis yang penting.
Alat-alat lainnya
Python adalah bahasa
pemrograman komputer tujuan umum. Terraform
adalah alat infrastruktur sebagai kode (IAc) HashiCorp yang membantu Anda membuat dan mengelola sumber daya cloud dan lokal.
Repositori kode
Repositori kode untuk AFT tersedia di GitHub AWS Control Tower Account Factory for Terraform
Praktik terbaik
Memahami model tanggung jawab AWS bersama
. Ikuti rekomendasi keamanan untuk AWS Control Tower. Untuk informasi selengkapnya, lihat Keamanan di AWS Control Tower.
Ikuti prinsip hak istimewa yang paling sedikit. Untuk informasi selengkapnya, lihat Menerapkan izin hak istimewa paling sedikit.
Membangun set izin khusus dan terfokus dan peran IAM untuk grup dan unit bisnis.
Epik
| Tugas | Deskripsi | Keterampilan yang dibutuhkan |
|---|---|---|
Buat peran IAM. | Di akun AWS Control Tower manajemen, gunakan Terraform untuk membuat peran IAM. Peran ini memiliki akses lintas akun dan kebijakan kepercayaan yang memungkinkan akses federasi dari penyedia identitas. Ini juga memiliki izin untuk memberikan akses ke akun lain melalui AWS Control Tower. Fungsi Lambda akan mengambil peran ini. Lakukan hal-hal berikut:
| AWS DevOps, arsitek Cloud |
Sesuaikan solusi untuk lingkungan Anda. |
| AWS DevOps, arsitek Cloud |
Menyebarkan solusinya. |
| AWS DevOps, arsitek Cloud |
Siapkan koneksi repositori kode. | Siapkan koneksi antara repositori kode tempat Anda akan menyimpan file konfigurasi dan file Anda. Akun AWS Untuk petunjuk, lihat Tambahkan penyedia sumber pihak ketiga ke saluran pipa yang digunakan CodeConnections dalam AWS CodePipeline dokumentasi. | AWS DevOps, arsitek Cloud |
| Tugas | Deskripsi | Keterampilan yang dibutuhkan |
|---|---|---|
Mulai pipeline AFT untuk menerapkan akun baru. | Ikuti petunjuk di Menyediakan akun baru dengan AFT untuk memulai pipeline yang membuat yang baru Akun AWS di AWS Control Tower lingkungan Anda. Tunggu proses pembuatan akun selesai. | AWS DevOps, arsitek Cloud |
Validasi perubahan. |
| AWS DevOps, arsitek Cloud |
Pemecahan masalah
| Isu | Solusi |
|---|---|
Penugasan set izin tidak berfungsi. | Pastikan parameter ARN grup, id organisasi, dan Lambda sudah benar. Sebagai contoh, lihat bagian Ikhtisar solusi dari pola ini. |
Memperbarui kode di repositori tidak memulai pipa. | Masalah ini terkait dengan konektivitas antara Anda Akun AWS dan repositori. Dalam Konsol Manajemen AWS, validasi bahwa koneksi aktif. Untuk informasi selengkapnya, lihat GitHub koneksi dalam AWS CodePipeline dokumentasi. |
Informasi tambahan
Mengintegrasikan dengan alat manajemen tiket
Anda dapat memilih untuk mengintegrasikan solusi ini dengan alat manajemen tiket atau masalah, seperti Jira atau ServiceNow. Diagram berikut menunjukkan contoh alur kerja untuk opsi ini. Anda dapat mengintegrasikan alat manajemen tiket dengan repositori solusi AFT dengan menggunakan konektor alat Anda. Untuk konektor Jira, lihat Mengintegrasikan Jiraaft-account-request GitHub Anda dapat mendesain alur kerja khusus apa pun yang memenuhi persyaratan kasus penggunaan Anda.
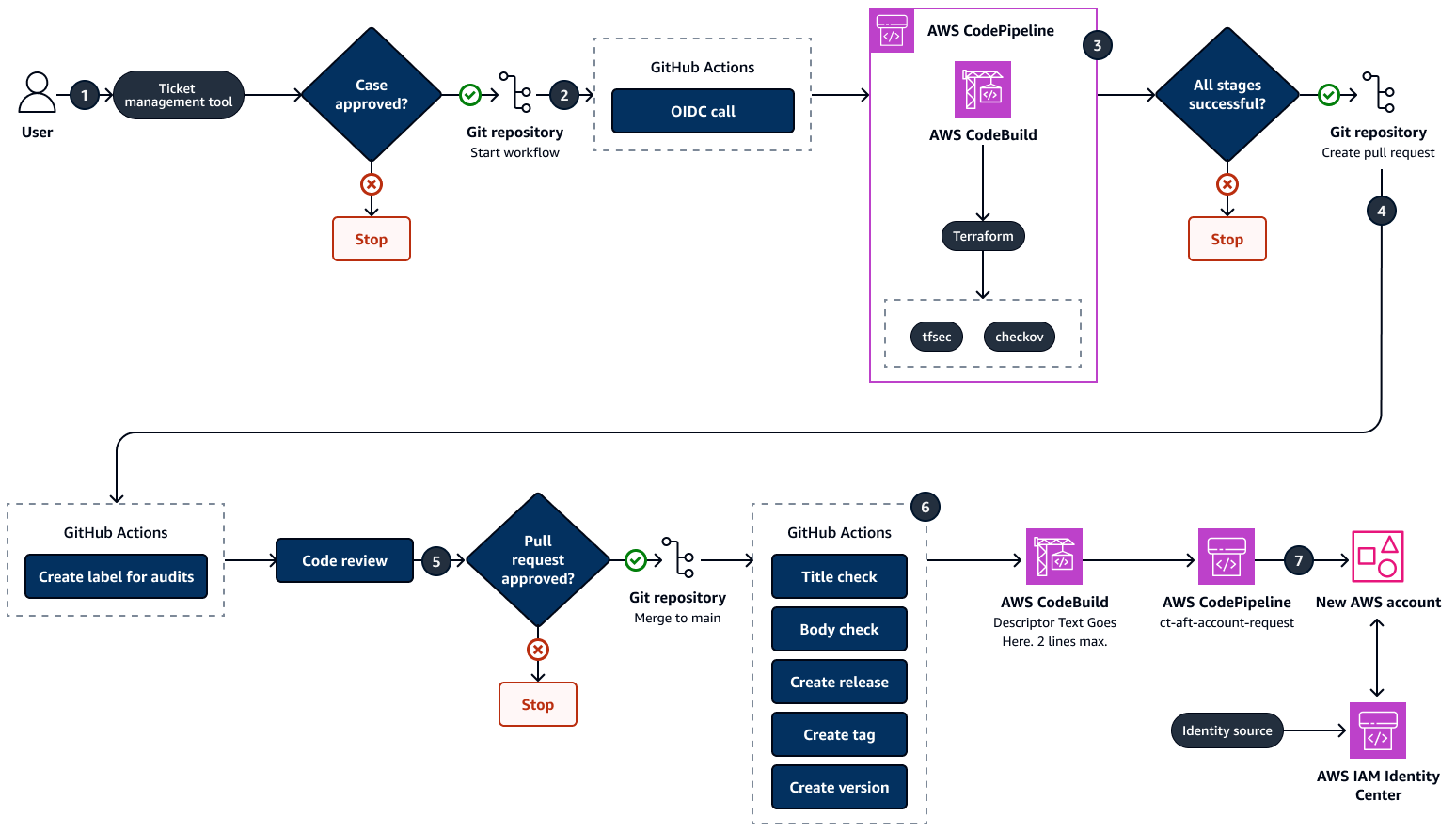
Diagram menunjukkan alur kerja berikut:
Pengguna meminta penetapan set izin khusus di alat manajemen tiket, seperti Jira.
Setelah kasus disetujui, alur kerja mulai memperbarui penetapan set izin. (Opsional) Anda dapat menggunakan plugin untuk otomatisasi kustom langkah ini.
Operator mengirim kode Terraform dengan parameter set izin yang diperbarui ke
aft-account-requestrepositori ke cabang pengembangan atau fitur.GitHub Tindakan dimulai AWS CodeBuild dengan menggunakan panggilan OpenID Connect (OIDC). CodeBuild melakukan pemindaian keamanan infrastruktur sebagai kode (IAc) dengan menggunakan alat seperti tfsec
dan checkov. Ini memperingatkan operator dari setiap pelanggaran keamanan. Jika tidak ditemukan pelanggaran, GitHub Actions akan membuat permintaan tarik otomatis dan menetapkan tinjauan kode kepada pemilik kode. Ini juga membuat tag untuk permintaan tarik.
Jika pemilik kode menyetujui peninjauan kode, alur kerja GitHub Tindakan lain akan dimulai. Ini memeriksa standar permintaan tarik, termasuk:
Jika judul permintaan tarik memenuhi persyaratan.
Jika badan permintaan tarik berisi nomor kasus yang disetujui.
Jika permintaan tarik ditandai dengan benar.
Jika permintaan tarik memenuhi standar, GitHub Actions akan memulai alur kerja produk AFT. Ini menggunakan memulai
ct-aft-account-requestpipa di AWS CodePipeline. Pipeline ini memulai mesin statusaft-account-provisioning-frameworkkustom di Step Functions. Mesin status ini berfungsi seperti yang dijelaskan sebelumnya di bagian Ikhtisar solusi dari pola ini.